How to Configure Firewall Rules
Firewalls are an essential part of modern security infrastructure, acting as the first line of defense against unauthorized access to your network or system. By filtering incoming and outgoing traffic, firewalls help prevent malicious activity, protect sensitive data, and ensure that only trusted users and applications can access your resources. To ensure optimal protection, it’s critical to configure firewall rules correctly.
In this article, we’ll cover the basics of firewall rules, their importance, and how to configure them effectively.
What Are Firewall Rules?
A firewall rule is a set of conditions that determines whether to allow or block specific network traffic. Firewall rules can control access based on several criteria, including:
- IP Addresses: Rules can specify traffic from or to specific IP addresses or address ranges.
- Ports: Rules can limit access to particular network ports (e.g., port 80 for HTTP, port 22 for SSH).
- Protocols: Rules can manage traffic based on network protocols (e.g., TCP, UDP, ICMP).
- Direction: Firewall rules apply to either incoming traffic (inbound) or outgoing traffic (outbound).
Types of Firewalls
Firewalls can be hardware or software-based. Some common types include:
- Network Firewalls: These are hardware devices that sit between your internal network and external networks, filtering traffic at the network level.
- Host-Based Firewalls: These are software firewalls installed on individual servers or computers, controlling traffic to and from that specific device.
Why Configure Firewall Rules?
Properly configuring firewall rules helps:
- Protect Against Unauthorized Access: By restricting access to specific IPs or ports, you can block malicious users or bots from accessing your systems.
- Limit Attack Surfaces: Blocking unnecessary services and ports reduces the number of potential entry points for attackers.
- Allow Legitimate Traffic: Ensure that legitimate users and applications can access your services by configuring rules that allow trusted IPs, ports, and protocols.
- Comply with Security Policies: Many industries have specific regulations regarding the protection of sensitive data, which often include the proper use of firewalls.
How to Configure Firewall Rules
The process of configuring firewall rules depends on whether you’re using a network firewall, a host-based firewall (like UFW on Linux).
Configuring Firewall Rules on Linux (UFW)
UFW (Uncomplicated Firewall) is a popular tool on Linux distributions like Ubuntu. It simplifies the process of setting up firewall rules.
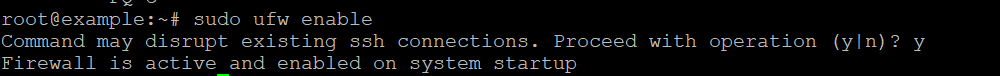
Step 1: Enable UFW
Before configuring any rules, ensure that UFW is enabled:
Step 2: Default Policies
It’s a good practice to set default policies. Most firewalls block all incoming traffic by default and allow all outgoing traffic:
This configuration ensures that only explicitly allowed services will be accessible from outside your system, while all outgoing traffic is permitted.
Step 3: Allow Specific Services
Next, you need to create rules to allow specific services or ports. For example:
- Allow SSH (port 22):
- Allow HTTP (port 80):
- Allow HTTPS (port 443):
You can also specify custom ports:
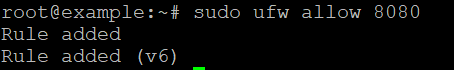
- Allow traffic on a custom port (e.g., 8080):
sudo ufw allow 8080Step 4: Allow Traffic from Specific IPs
To allow traffic from a specific IP address (e.g., for SSH access), use:
sudo ufw allow from 192.168.1.100 to any port 22
This rule restricts SSH access to the IP address 192.168.1.100.
Step 5: Deny Traffic from Specific IPs
If you want to block traffic from a specific IP or network, you can use the following command:
This blocks all traffic from the IP address 203.0.113.1.
Step 6: View Active Rules
To view your currently active firewall rules, use:
Step 7: Disable or Remove Rules
To remove or disable a specific rule, you can use:
This command removes the rule allowing SSH on port 22.
Step 8: Reload the Firewall
After making changes to the firewall configuration, ensure that the rules are active by reloading the firewall:
Configuring Firewall Rules in Windows
Windows has a built-in firewall, which can be configured via the Windows Defender Firewall interface or via the command line using netsh.
Step 1: Open Windows Defender Firewall
- Go to the Control Panel.
- Click on System and Security.
- Select Windows Defender Firewall.
Step 2: Create Inbound and Outbound Rules
- In the left-hand menu, click Advanced Settings.
- In the Windows Defender Firewall with Advanced Security window, select either Inbound Rules or Outbound Rules, depending on what you want to configure.
- Click New Rule on the right-hand side.
- Choose the type of rule:
- Port: To open specific network ports (e.g., 80, 443).
- Program: To allow or block specific applications.
- Custom: To configure more advanced rules.
- Follow the prompts to specify the port, program, or IP address, then choose whether to allow or block the connection.
Step 3: Apply and Test the Rules
Once you’ve added the firewall rule, make sure to apply it, then test the connection by accessing the relevant service or application to ensure the rule is working as expected.
Conclusion
Configuring firewall rules is an essential aspect of securing your network and systems from unauthorized access and cyber threats. Whether you’re managing a Linux server with UFW, setting up rules in Windows Defender, properly configured firewall rules help safeguard your resources and ensure that only legitimate traffic reaches your system. By following best practices and regularly reviewing your firewall rules, you can create a robust security defense for your applications and infrastructure.