Configure a Firewall with Firewalld
For those using Linux hosting from AlexHost, protecting your server with a properly configured firewall is very important. AlexHost provides stable and performance-optimized hosting, giving you full control over your server’s security settings. With AlexHost, you can use tools like Firewalld to strengthen your server’s security against unauthorized access and potential threats. This guide will help you install, configure, and manage Firewalld on your Linux server, allowing you to maintain safe and secure hosting on AlexHost’s trusted platform.
Configure a Firewall with Firewalld
In today’s digital age, securing your server and network is crucial. A firewall acts as a barrier between your trusted internal network and untrusted external networks, controlling incoming and outgoing traffic based on predetermined security rules. Firewalld is a dynamic firewall management tool available on many Linux distributions, such as CentOS, Fedora, and RHEL. This article will guide you through the basics of installing, configuring, and managing a firewall using Firewalld. For a more in-depth understanding and additional resources, you can visit our comprehensive guide: An Introduction to Firewalld.
Installing Firewalld
On most Linux distributions, Firewalld is included in the default repositories. Here’s how to install it on popular distributions:
For CentOS/RHEL:
For Fedora:
For Debian/Ubuntu:
While Firewalld is primarily used on RHEL-based systems, it can also be installed on Debian-based systems:
Starting and Enabling Firewalld
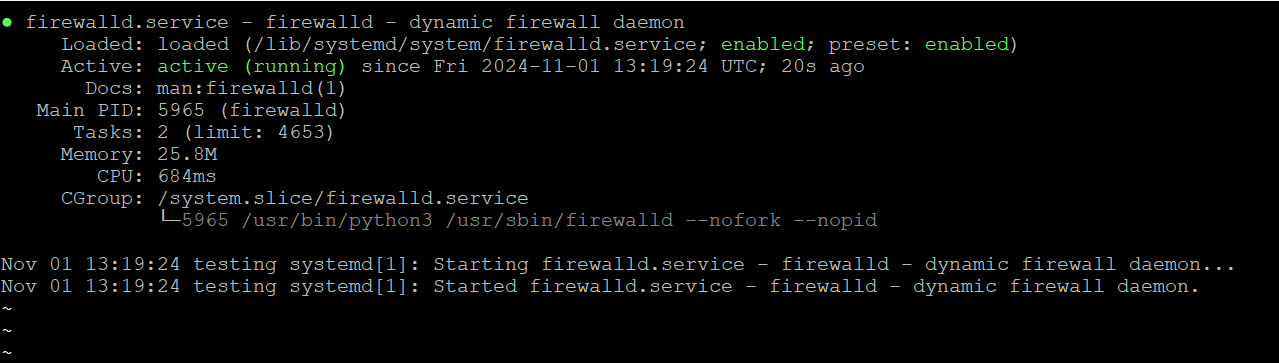
After installation, you need to start and enable Firewalld to run at boot.
You can check the status of Firewalld with:
Basic Firewalld Commands
Firewalld uses the firewall-cmd command for configuration and management. Below are some fundamental commands to get you started.
Check the Default Zone
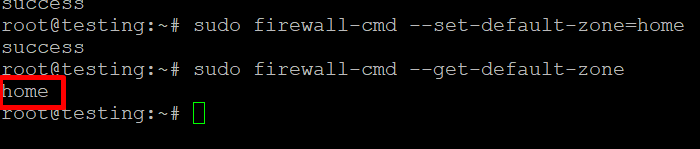
Firewalld uses zones to manage rules. You can check the default zone with:
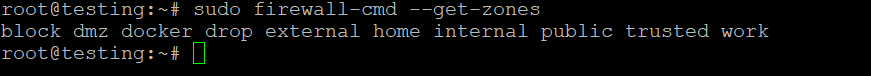
List All Zones
To see all available zones, use:
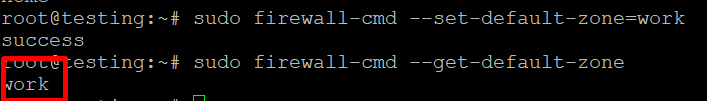
Set the Default Zone
You can change the default zone with:
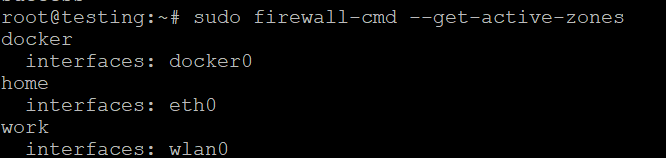
Get Active Zones
To see which zones are currently active and their associated interfaces, run:
Configuring Firewalld
Adding Services
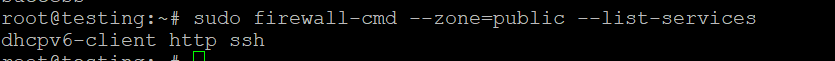
Firewalld allows you to easily add services to a zone. For example, to allow HTTP traffic in the public zone, use:
To apply the changes, reload Firewalld:
Removing Services
If you need to remove a service, such as HTTPS, you can do so with:
Opening Specific Ports
You can open specific ports (e.g., port 8080) in a zone:
Closing Ports
To close a port, use:
Reloading Firewalld
Whenever you make changes, it’s essential to reload Firewalld to apply those changes:
Working with Zones
Firewalld supports different zones that can be applied to interfaces. Each zone defines a level of trust for network connections. Here are some commonly used zones:
- public: For use in public areas, the default zone for untrusted connections.
- home: For home networks where you trust other hosts.
- work: For work networks, similar to home but less trusted.
- dmz: For servers that should be accessible from the outside but need to be isolated from the internal network.
Advanced Configuration: Rich Rules
Firewalld also supports rich rules, allowing for more complex configurations. For example, to allow SSH from a specific IP address:
Monitoring Firewalld
To view the current configuration and active rules, use:
Conclusion
Firewalld provides an intuitive way to manage your firewall configurations on Linux. By utilizing zones, services, and rich rules, you can effectively control access to your system and enhance security. Remember to periodically review and update your firewall rules to adapt to changes in your network and security posture. With this guide, you are now equipped to configure and manage a firewall using Firewalld effectively.